Batman Uses Kubescape for the First Time!
adding kubescape to my utility belt
Batman faces multiple threats everyday including criminals, crazy villains and corrupt politicians. But today he has a bigger problem. Possibly, the most dangerous of them all - Security.
Batman stores the information of every criminal in his Batcomputer. This information is stored in the form of containers. Each container contain packages of information related to different villains. Joker is after this information. Batman has to find a way to secure his Kubernetes clusters!

Prerequisites:
- Docker: Docker is a software platform that allows you to build, test, and deploy applications quickly. This is achieved using Containers. To get started with docker you can click here.
- Kubernetes: Kubernetes, also known as K8s, is an open-source system for automating deployment, scaling, and management of these containerized applications. To learn more about kubernetes and it's various aspects, click here.
Why Kubernetes Security is Important?
Your system can have countless number of containers. Although using containers gives you the opportunity to access the power of microservices and greater speed, using them can also create security vulnerabilities and expose your application to attackers like Joker.

Batman's Past Experiences with Security:
During batman's first year as a crime fighting vigilante, A user called as riddler616 gained access to batcomputer due to some kubernetes misconfigurations. The attacker then stole this data and sold it to various criminal organizations. Batman wished if there was some way to secure his K8's clusters!
Batman's billionaire best friend Elon musk also had a very bad experience with K8's security. In February 2018, Crypto-mining malware infiltrated Tesla's Kubernetes console. The attack was possible because the console wasn't password protected. Consequently, hackers leveraged one of Tesla's pods to do crypto-mining.
"The hackers had infiltrated Tesla's Kubernetes console, which was not password protected. Within one Kubernetes pod, access credentials were exposed to Tesla's AWS environment, which contained an Amazon S3 (Amazon Simple Storage Service) bucket that had sensitive data such as telemetry." - RedLock.
Kubescape
Enter Kubescape! Kubescape is a K8s open-source tool providing a multi-cloud K8s single pane of glass, including risk analysis, security compliance, RBAC visualizer and image vulnerabilities scanning. Kubescape scans K8s clusters, YAML files, and HELM charts, detecting misconfigurations according to multiple frameworks.
Kubescape quickly became one of Batman's favorite gadgets due to its easy-to-use CLI interface, flexible output formats, and automated scanning capabilities, saving Kubernetes users and admins’ precious time, effort, and resources.
Kubescape integrates natively with other DevOps tools, including Jenkins, CircleCI, Github workflows, Prometheus, and Slack, and supports multi-cloud K8s deployments like EKS, GKE, and AKS.
Kubescape will help Batman safeguard his K8's clusters against Joker and other security threats.
Installation
Install on Windows
To install Kubescape on a windows machine, open up your Windows powershell (powershell, not command prompt) and paste the following command:
iwr -useb https://raw.githubusercontent.com/armosec/kubescape/master/install.ps1 | iex
Install on MacOS:
Batman knows everything! To install kubescape on your MacOS machine paste the following commands:
brew tap armosec/kubescape
brew install kubescape
(Batman doesn't use macOS)
Scan your cluster
Moment of truth. It's time for batman to check if there are any vulnerabilities in his cluster. We don't want joker or any vigilante in gotham to threaten us!
To scan your cluster use:
kubescape scan --submit --enable-host-scan
...and Boom!
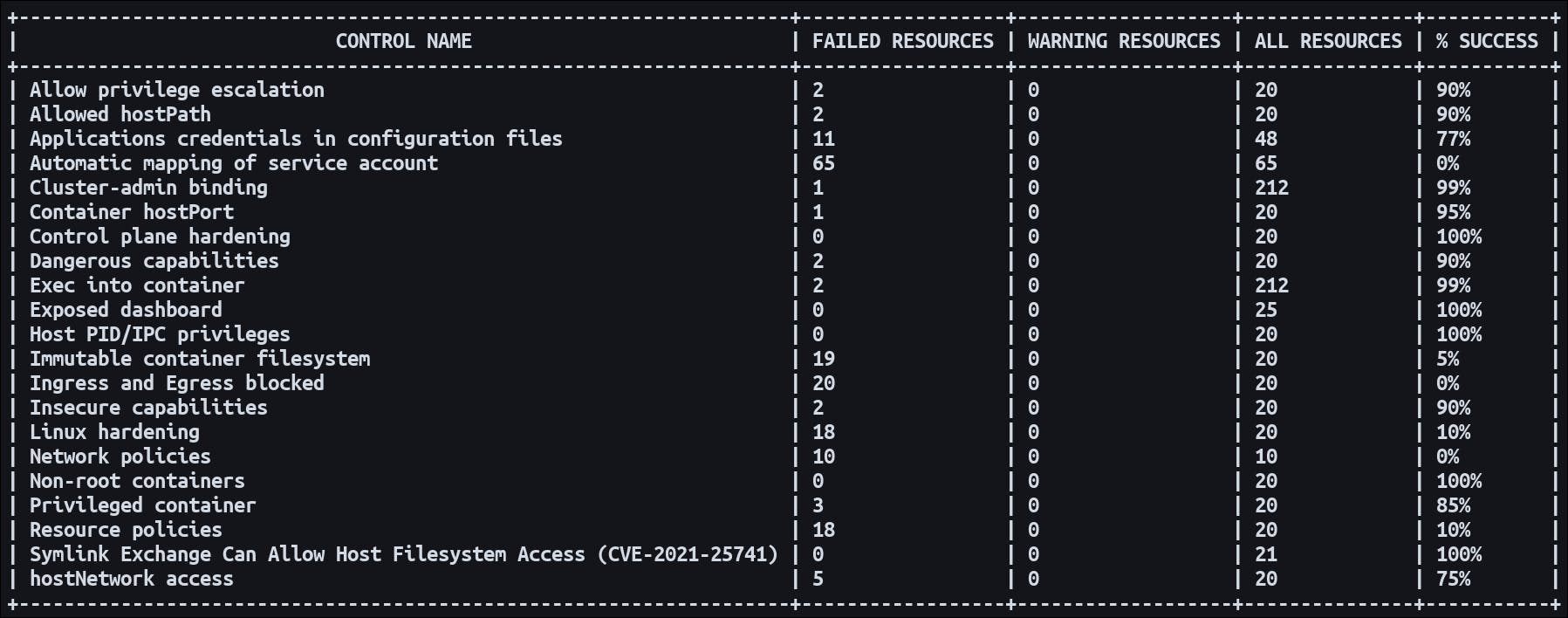
Seems like batman has a long way to go !
Kubescape Dashboard
Even batman finds it overwhelming to control everything from the command line ! To solve this issue, Kubescape has provided us with Kubescape dashboard. An easy to navigate dashboard which makes things significantly easy for all of us.
To sign up on this portal, click here.
Your kubescape dashboard will look something like this
Kubescape Components
Configuration Scanning
You must have become familiar with this aspect of Kubescape by now. Configuration scanning allows us to identify the misconfigurations and vulnerabilities in the cluster, containers and pods.
Configuration scanning can also give more confidence to the DevOps team to develop and deploy the applications on a Kubernetes cluster.
Image Scanning
Image scanning means the process of analyzing the contents and the build process of a container image in order to detect security issues, vulnerabilities or bad practice. It's critical to perform a image scan nowadays because it has become a important component of Devops security practice.
Kubescape helps us in scanning our image and finding various severities in it. The severities can range from either critical, high, medium to low, negligible and unknown.
RBAC Visualizer
Role-based access control (RBAC) is a method of regulating access to computer or network resources based on the roles of individual users within your organization.
RBAC is an authorization mechanism for managing permissions around Kubernetes resources. RBAC allows configuration of flexible authorization policies that can be updated without cluster restarts.
In Kubescape, you can add your query and investigate multiple aspects of it in your dashboard.
Conclusion

Kubescape saves the day again! Batman has secured his K8's cluster from Joker thanks to amazing services provided by Kubescape. K8's cluster scanning skills reported batman of various threats and vulnerability leaks.
After getting familiar with various threats and suggestions by kubescape Batman will definitely use kubescape again when creating new K8's clusters.
Kubescape truly solves the security issues of batman as well as various developers around the world.
